-
What This Graph Shows
-
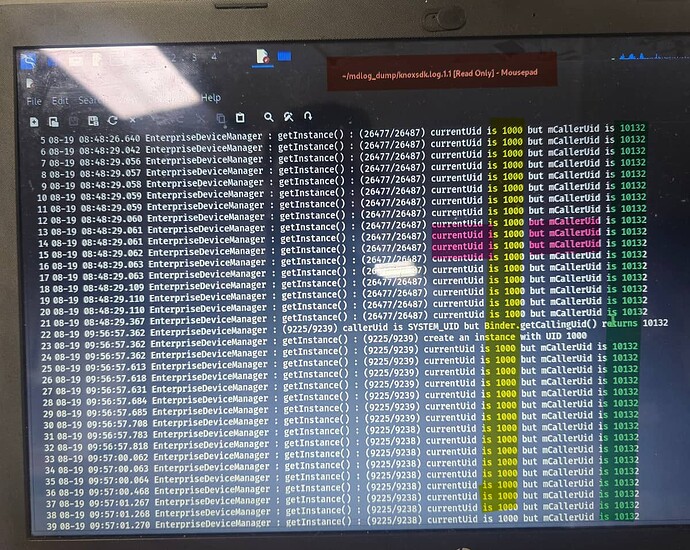
 UID 10132 getInstance() calls: backend process injecting into your UID 1000 context
UID 10132 getInstance() calls: backend process injecting into your UID 1000 context -
 EnterpriseDeviceManager masquerade: UID 1000 labeled events triggered by UID 10132
EnterpriseDeviceManager masquerade: UID 1000 labeled events triggered by UID 10132 -
 CloudConfigurationManagerService confirmations: backend handshake locking in policy state
CloudConfigurationManagerService confirmations: backend handshake locking in policy state
-
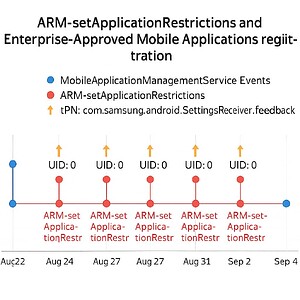
What This Graph Shows
 ARM-setApplicationRestrictions (orange hexagons): backend policy pushes under UID 0
ARM-setApplicationRestrictions (orange hexagons): backend policy pushes under UID 0 EAM Registration (blue squares): MobileApplicationManagementService logging enterprise agents (MDM, Intune, SDS EMM)
EAM Registration (blue squares): MobileApplicationManagementService logging enterprise agents (MDM, Intune, SDS EMM) Telemetry Routing (tPN.feedback, red circles): enforcement disguised as feedback
Telemetry Routing (tPN.feedback, red circles): enforcement disguised as feedback System Trigger (cPN: android/system, light blue circles): backend activation point
System Trigger (cPN: android/system, light blue circles): backend activation point Chained Enforcement Cycles: each sequence shows EAM registration → ARM push → telemetry route → system trigger
Chained Enforcement Cycles: each sequence shows EAM registration → ARM push → telemetry route → system trigger
Looking for Advice , this doesn’t seem right knox is using my UID to move behind it seems why? I was hoping come on here and we could figure it out all this is just the opening, this normal?